Threats from Malware and Ransomware are Rapidly Growing
 With the increase in Malware and Ransomware attacks, reliability and data integrity are now at the forefront of business concerns and a primary challenge for businesses to solve. In this article, we review Ransomware detection and recovery architectures,
With the increase in Malware and Ransomware attacks, reliability and data integrity are now at the forefront of business concerns and a primary challenge for businesses to solve. In this article, we review Ransomware detection and recovery architectures,
including immutable backups and air-gapped systems.
We also review the HPE Shadowbase Ransomware architecture that assists businesses with thwarting this growing set of unique challenges and how the solution is evolving.
Note: This article is based on a presentation and demo given by Gravic at the Connect NonStop Technical Boot Camp in September 2023. Text from various slides is duplicated on the page to allow our international readers to use translation tools.
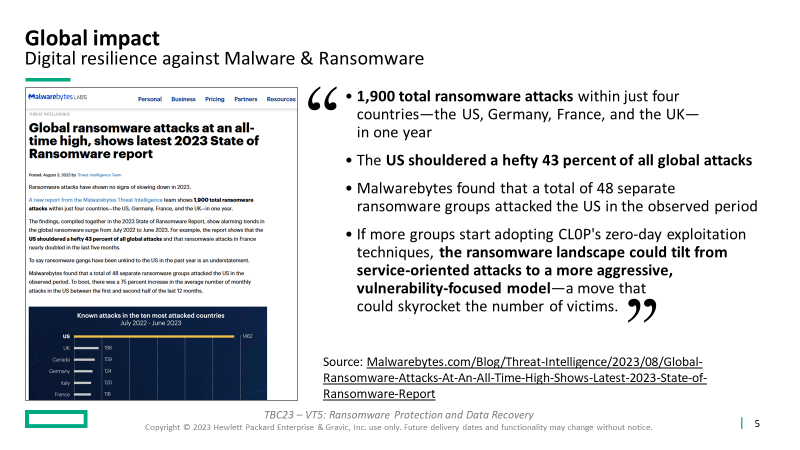
At the 2023 HPE Discover show, Veeam presented research from surveying thousands of their customers:
- “93% of attacks targeted backup repositories”
- “4% of Ransomware victims paid the ransom and could not recover their data”
- “77% of payments were covered by insurance”
- “On average, only 66% of affected data was recoverable”
Malware and Ransomware have a global impact for businesses of all kinds and are spurring regulatory mandates across the globe.
- Digital resilience
- According to the European Union’s DORA Act, digital resilience is the “protection, detection, containment, recovery and repair capabilities against information and communication technology (ICT) related incidents”
- U. S. Executive Orders have been released to address digital resilience from an infrastructure and hardware perspective, with many more regulations to come as DORA and the digital resilience landscape evolves
- Ransomware
- New approaches are available to combat these challenges such as “immutable backups” and “air-gapped” systems
- HPE NonStop provides a layer of protection with TMF-audited applications
- Data replication using audited environments will not spread ransomware
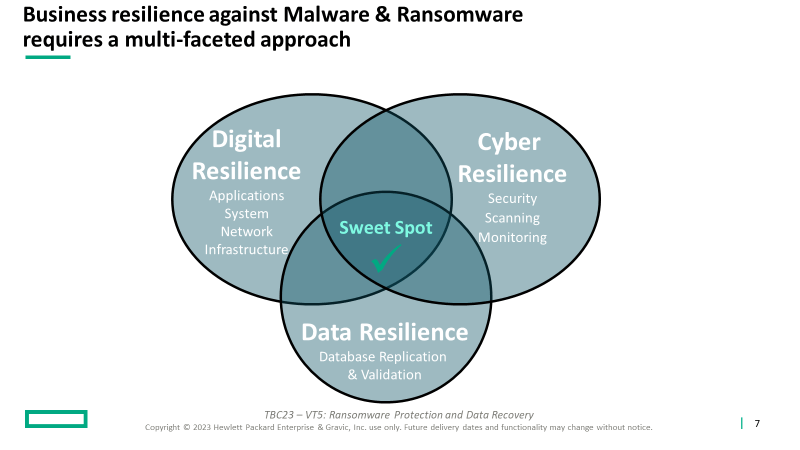
Business resilience solutions that can successfully defend against Malware and Ransomware require a multi-faceted approach. For these three key pieces, these are their main areas of focus:
-
- Digital Resilience – redundant and resilient Infrastructure
- Cyber Resilience – monitoring system activity and traffic and securing the environment from unauthorized access
- Data Resilience – database replication and validation
-
- Always remember the 3-2-1-1 rule:
- 3 data copies
- 2 different storage media
- at least 1 copy off-site
- at least 1 in immutable storage (managed by different staff)
Background
Many HPE NonStop customers are easily overwhelmed when strategizing Malware and Ransomware recovery solutions. A great place to start is by defining the problem:
1. Know your enemy – Malware and Ransomware are similar, but different:
-
-
- Malware – software that is specifically designed to disrupt, damage, or gain unauthorized access to a computer system (dictionary.com)
- Ransomware – malicious software designed to block access to a computer system until a sum of money is paid (dictionary.com)
2. Resilience against each is (a bit) different – multiple products are required to create an overarching solution and must be coordinated.
3. Detection and recovery is not the same thing as prevention
-
-
- Today, state-of-the-art is post-event detection and recovery
- The future needs to focus on identifying the attack early and preventing it from having an impact
4. HPE Shadowbase software currently provides data resilience for detection and recovery.
5. However, HPE Shadowbase software is only one piece of the solution – for example, malware that stealthily steals data requires additional counter-measures.
6. The Gravic Validation Architecture (VA) is a new technology being developed to immediately detect and prevent data corruption.
On HPE NonStop, TMF is your first line of defense!
Non-audited data does not have the same advantages, capabilities, nor protection.
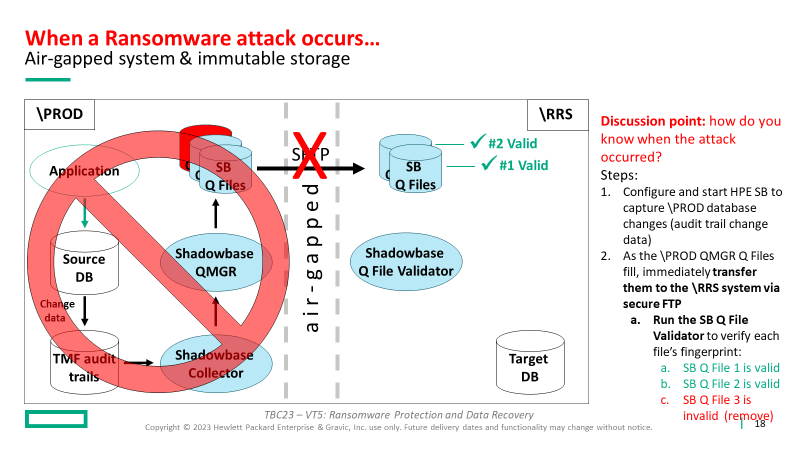
In a non-audited environment, if malware invaded and performed data tampering – how would you know?
Using TMF guarantees all database changes are logged and therefore, can be leveraged for recovery. Simply put, this leverage is not always possible in a non-audited environment.
HPE Shadowbase Digital Resilience Provides Unique Capabilities
HPE Shadowbase software integrates with TMF to extract database change data, fingerprints messages to detect interprocess message tampering, and fingerprints its intermediate Queue Files to detect data tampering.
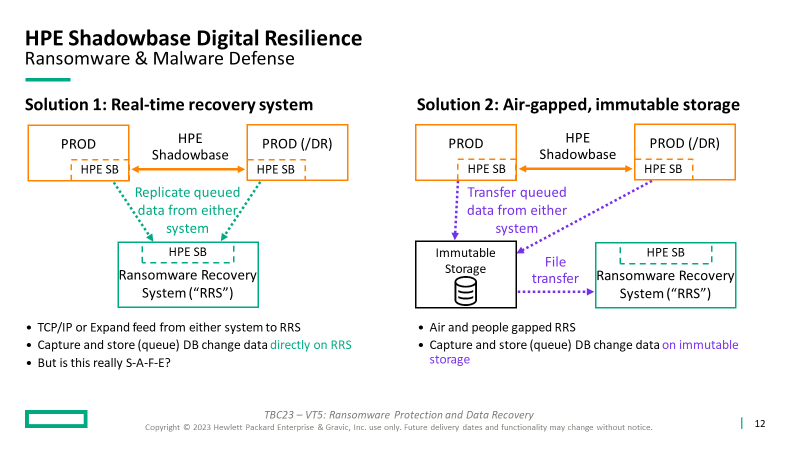
Both options:
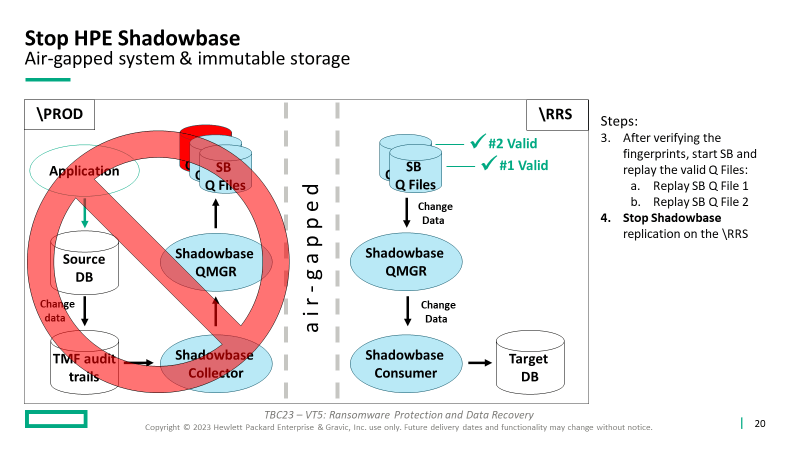
- The customer decides how often to synchronize the RRS database to bring it current
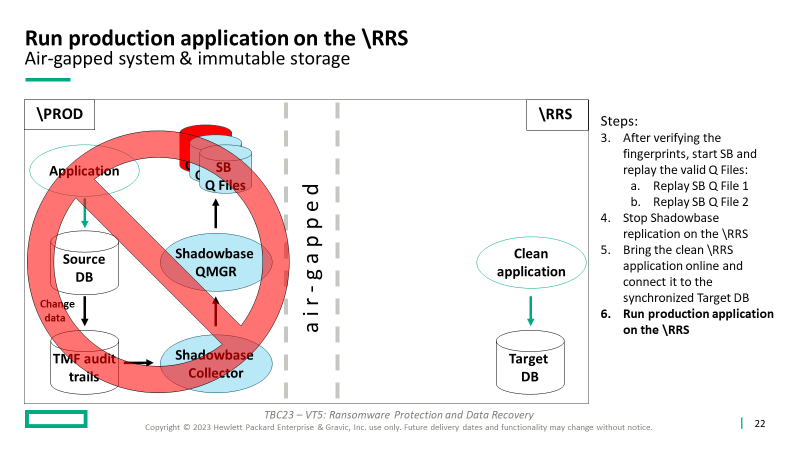
- After an attack, recover the application and operations on the RRS to continue production processing, which supports subsequent forensics and root cause analysis on the compromised system
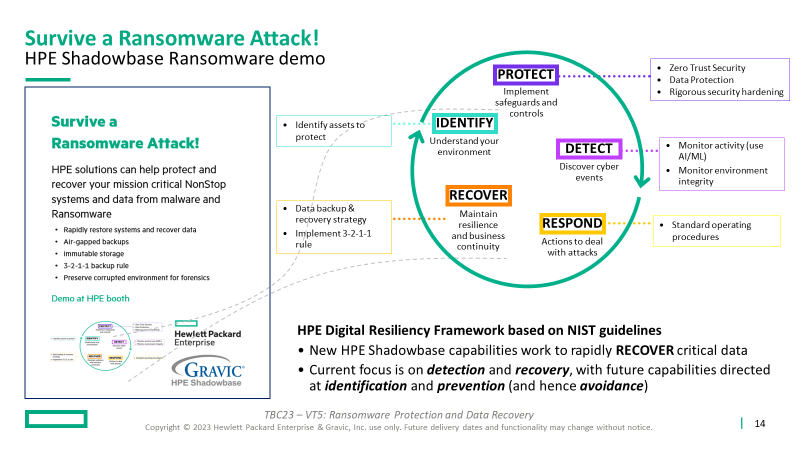
How to Survive a Ransomware Attack
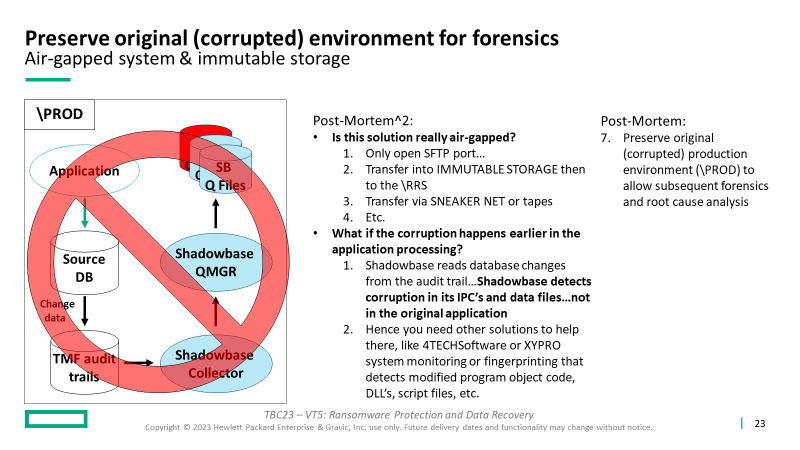
This solution features key products available from the HPE product suite, including HPE Shadowbase Ransomware, to build out a malware and ransomware defense architecture to allow your business to survive, successfully recover from an attack, and preserve the original infected environment for subsequent analysis and forensics.
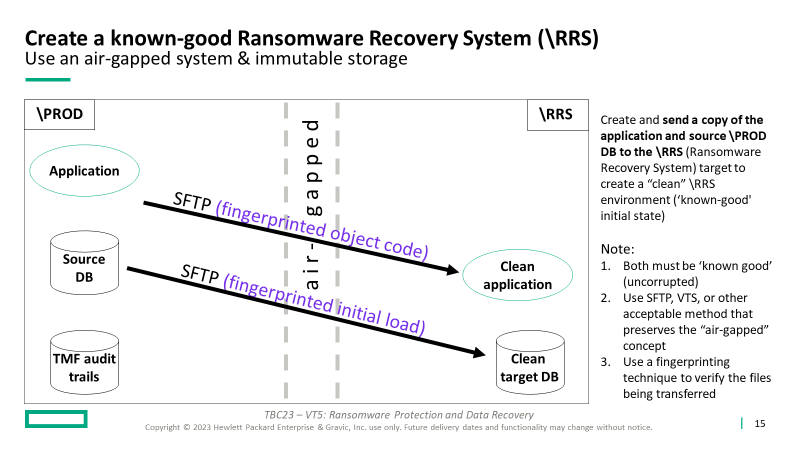
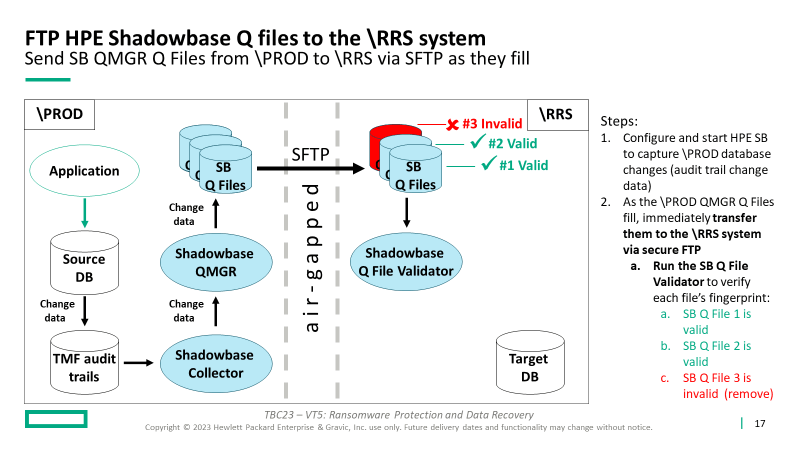
Initially, and periodically, create and send a copy of the application and source \PROD DB to the \RRS (Ransomware Recovery System) target to create a “clean” \RRS environment (‘known good’ initial state).
Note:
- Both must be ‘known good’ (uncorrupted)
- Use SFTP, VTS, or another acceptable method that preserves the “air-gapped” concept (including tapes and “sneaker net” if you prefer)
- Use a fingerprinting technique to verify the files being transferred
 With the increase in Malware and Ransomware attacks, reliability and data integrity are now at the forefront of business concerns and a primary challenge for businesses to solve. In this article, we review Ransomware detection and recovery architectures,
With the increase in Malware and Ransomware attacks, reliability and data integrity are now at the forefront of business concerns and a primary challenge for businesses to solve. In this article, we review Ransomware detection and recovery architectures,