Prevent Fraudulent Activity for Online Banking on IBM Db2®
Share This!
 Copy link to clipboard
Copy link to clipboard Email link
Email link Print
Print
Situation
A European bank provides online account access to its customers for a banking application that runs on an IBM z/OS mainframe system. Fraud occurs and is difficult to identify and prosecute. Conspiracy is not sufficient grounds for prosecution in this country.
The intent to commit a crime is not sufficient; the crime must actually be attempted for prosecution. Fraudulent financial activity is increasing in the region, particularly in online banking.
Problem
- This situation was costing the bank a lot of money since it was often unsuccessful in preventing the fraud.
- It was difficult to detect the crime and gather the information to assist authorities. The bank needed a straight-forward method to integrate a Linux-based fraud-scoring application without having to rewrite (or modify) its applications.
Solution
- Use HPE Shadowbase Application Integration to integrate the IBM z/OS banking activity in real-time with a Linux-based fraud-scoring application, to detect and prevent fraud before it occurs.
- Use HPE Shadowbase User Exits (where custom code is embedded into the replication engine) to seamlessly perform the integration.
- Leverage IBM Data Event Publisher (IDEP) and MQ Series for IBM Db2 event extraction, and delivery to the Shadowbase Fraud Interface User Exit Logic.
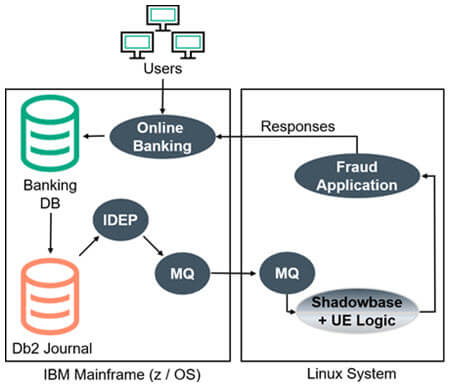
Figure 1 — The Bank’s Fraud Detection Architecture
Outcomes
- Reduces costs from fraudulent activity
- Enables the bank to demonstrate actual, attempted fraud (with the HPE Shadowbase User Exit Logic)
- Simplifies identifying crimes, using the online fraud-scoring application, and denies authorization for suspicious activity
- Helps stem the problem by increasing prosecution and conviction rates
- Avoids having to install any HPE Shadowbase components on the IBM mainframe environment
HPE Shadowbase Product of Interest
- HPE Shadowbase Basic Application Software 1-8 core or 9+ core (WSA51V6T1/T2)
Contact us or your HPE Shadowbase representative, and learn how Shadowbase software will benefit you.
Further Reading
Related Case Study:  Winning the Battle Against Internet Banking Fraud by Leveraging Real-Time Data and Application Integration
Winning the Battle Against Internet Banking Fraud by Leveraging Real-Time Data and Application Integration
Related White Paper:  HPE Shadowbase Streams for Application Integration
HPE Shadowbase Streams for Application Integration
Related Solution Briefs:


![]() Winning the Battle Against Internet Banking Fraud by Leveraging Real-Time Data and Application Integration
Winning the Battle Against Internet Banking Fraud by Leveraging Real-Time Data and Application Integration![]() HPE Shadowbase Streams for Application Integration
HPE Shadowbase Streams for Application Integration