- About
- Solutions
- Essentials
- Utilities
- Publications
- Product Delivery
- Support

Available for the HPE NonStop Server platform as a source (Enscribe, NonStop SQL/MP, NonStop SQL/MX), HPE Shadowbase Audit Log (SAL) software creates a searchable archival database of transactional activity (e.g., inserts, updates, and deletes) on a reporting database for application change data auditing purposes. The reporting database is created on an off-platform target database (for example, Oracle, SAP HANA, or SQL Server).
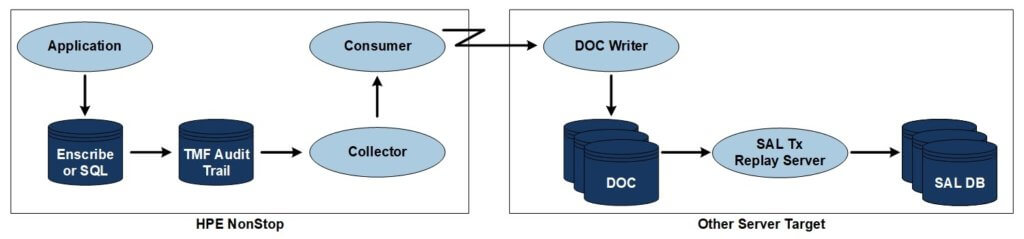
Figure 1 — Sample Shadowbase Audit Log Architecture
When configured, SAL software will replicate the selected HPE NonStop TMF audit trail source database change activity to the target reporting database, storing the change information as a series of rows, one for each application database change (e.g., one per insert, update, and delete statement).
This information allows you to search and review, historically, what data was changed, and when, in the source database.

SAR software mines the TMF audit trail activity, showing the transactional database changes the application made, when they were made, which database files and tables were affected. This enables investigation into how the data is being changed.
Both current and historical transactional information can be analyzed using a variety of search criteria. All of these features are available using a simple, easy to learn, SQL-like command line interface.
When used during the development of code, for example, one can generate a report showing the exact order or sequence in which the application applied changes to the database.
These database changes can be analyzed to make sure the code is working properly, and that the application is working as desired (based upon the correct implementation of the intended design algorithm or business rule).
SAR is particularly useful for analyzing how a vendor-supplied software is making database changes (e.g., for cases where you do not have access to the source code) so that you can see exactly how the application is changing the database for each transaction it performs.
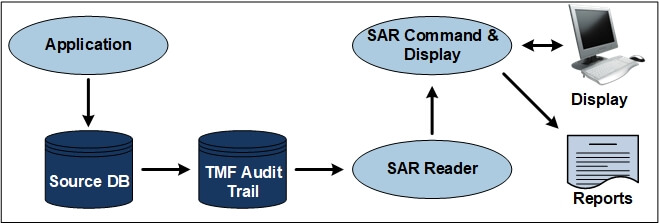
Figure 2 — Sample Shadowbase Audit Reader Architecture
When run, SAR software will extract the database changes from the TMF Audit Trail, apply any supplied WHERE clause for filtering, and display the results on either the terminal or in the report.